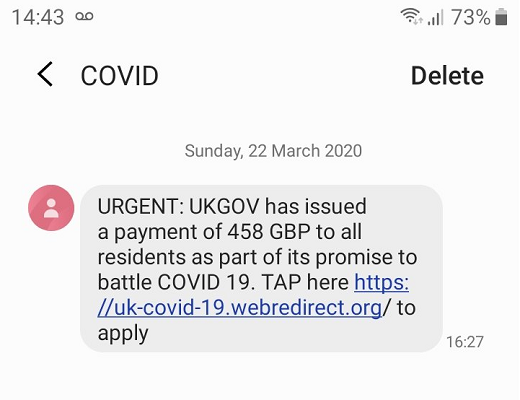
Hackers promise victims fake coronavirus payments and rebates, warns U.S. and UK government
Hackers are taking advantage of the coronavirus scare to lure people into clicking on links in text messages and emails that promise to take them to sites where they can sign up for, or even collect, relief funds from their government.
The problem has grown so widespread, that three global agencies, the United States Department of Homeland Security (DHS), the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom's National Cyber Security Centre (NCSC) released a join statement Wednesday morning to warn residents.
No one appears safe from these online attacks, which the government agencies say are growing, particularly as more people are working from home and using what the three call "potentially vulnerable services, such as virtual private networks."
"[Advanced persistent threat] groups and cybercriminals are targeting individuals, small and medium enterprises, and large organizations with COVID-19 related scams and phishing emails," they wrote.
Key things to watch for are messages that include the subject of COVID-19 or coronavirus. These seem to be targeting new remote access set-ups that have grown in use over the past months. Also being watched are new URLs that have been registered using words referring to coronavirus or COVID-19.
Hackers typically include links or downloads like a Microsoft Excel spreadsheet in these messages that can install malware on a computer. The links may be telling them to sign up for relief funds, or be cloaked as a coronavirus tracker. Typically these emails are also spoofed — either portending to be coming from an official group — as if they're sent by a group like the World Health Organization (WHO) or they have an official title on their email address like, "Dr."
Instead of getting information, victims may end up downloading programs that can share their desktop with a hacker, or give them remote access control. There are also malware programs that can shut down a computer or network demanding a fee to open the network back up, called ransomware.
VPNs, virtual private networks, are also being closely targeted, including those from Citrix, Pulse Secure, Fortinet and Palo Alto. And of course video conferencing tools including Zoom and Microsoft Teams, are already falling victim to attacks, with hackers hijacking these calls.
What can you do?
Anyone who thinks they've fallen victim to a fake email or text phishing attack should certainly, immediately, change their password to any account used, and also take the time then to secure other digital accounts.
Second, enabling passwords or using the waiting room feature on Zoom, for example, can help to keep people from hijacking video conferences. Also, sending the links for these calls directly to participants instead of posting them publicly is a good idea as well.
Third, keep all software and apps updated with the most recent versions as they're made available.
Fourth, most agencies — especially regarding relief funds — will not reach out to people directly. If you receive an email promising money, it's better to go online and type the name of the agency into a search engine, and from there go directly to their site.
Ultimately, the agencies note that people should expect "for a percentage of phishing attacks to be successful," they wrote. "Planning for these incidents all help minimize the damage caused."